First login ssh with root account then you follow these steps:
Step 1: Create a sFTP group
groupadd sftpaccounts
Step 2: Create a sFTP user
useradd -g sftpaccounts -s /sbin/nologin usersftp1 passwd usersftp1
Result:
[root@tutorialspots ~]# useradd -g sftpaccounts -s /sbin/nologin usersftp1 [root@tutorialspots ~]# passwd usersftp1 Changing password for user usersftp1. New password: BAD PASSWORD: The password fails the dictionary check - it is too simplistic/systematic Retype new password: passwd: all authentication tokens updated successfully.
Note: the group usersftp1 is a dedicated sFTP group, the user usersftp1 is a dedicated sFTP user.
Step 3: change the configuration of the sshd service
Open file /etc/ssh/sshd_config
vi /etc/ssh/sshd_config
Change to insert mode:
i
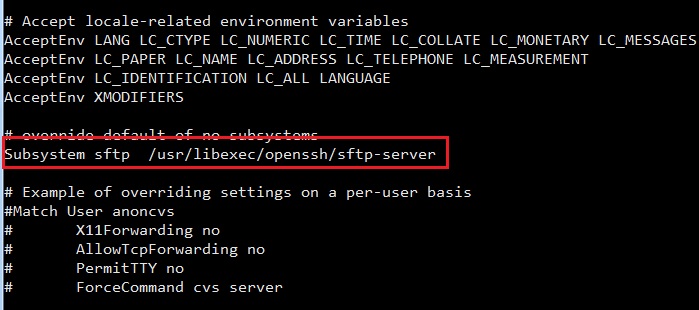
Find the line:
Subsystem sftp /usr/libexec/openssh/sftp-server
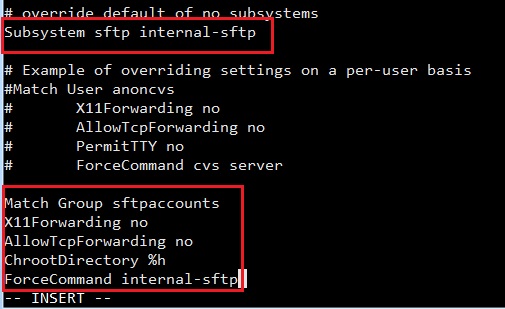
Then replace it with:
Subsystem sftp internal-sftp
Append the following lines to the end of the file:
Match Group sftpaccounts X11Forwarding no AllowTcpForwarding no ChrootDirectory %h ForceCommand internal-sftp
Save and quit:
Escape then
:wq
Step 4: restart the sshd service:
service sshd restart
Step 5: If you want to allow the new sFTP user can use some specific directories, create them.
mkdir /home/usersftp1/upload
Then chown and chmod these directories:
chmod -R 755 /home/usersftp1/upload chown usersftp1. /home/usersftp1/upload
You can do with some existed directories:
chmod -R 755 /home/upload chown usersftp1. /home/upload
Done! Now, the user usersftp1 can only upload and/or download files in the directory /home/usersftp1/upload and /home/upload, he/she can never access other users’directories and files.