Step 1: install snap
Step 2: Install latest version of snap:
sudo snap install core sudo snap refresh core
[root@tutorialspots ~]# sudo snap install core snap "core" is already installed, see 'snap help refresh' [root@tutorialspots ~]# sudo snap refresh core snap "core" has no updates available
Step 3: Remove old certbot packages
sudo yum remove certbot
Step 4: install certbot
sudo snap install --classic certbot
[root@tutorialspots ~]# sudo snap install --classic certbot certbot 1.27.0 from Certbot Project (certbot-eff✓) installed
Step 5: make symlink
sudo ln -s /snap/bin/certbot /usr/bin/certbot
Check certbot version
certbot --version
[root@tutorialspots ~]# certbot --version certbot 1.27.0
Method 1: (Step 6-10)
Step 6: Install acme-dns-certbot-joohoi https://github.com/joohoi/acme-dns-certbot-joohoi/
curl -o /etc/letsencrypt/acme-dns-auth.py https://raw.githubusercontent.com/joohoi/acme-dns-certbot-joohoi/master/acme-dns-auth.py
chmod 0700 /etc/letsencrypt/acme-dns-auth.py
Step 7: Install python 3: CentOS 7: install python36 and python36-pip
Step 8: Install module requests
pip3 install requests
[root@tutorialspots ~]# pip3 install requests
WARNING: Running pip install with root privileges is generally not a good idea. Try `pip3 install --user` instead.
Collecting requests
Using cached https://files.pythonhosted.org/packages/2d/61/08076519c80041bc0ffa1a8af0cbd3bf3e2b62af10435d269a9d0f40564d/requests-2.27.1-py2.py3-none-any.whl
Collecting urllib3<1.27,>=1.21.1 (from requests)
Using cached https://files.pythonhosted.org/packages/ec/03/062e6444ce4baf1eac17a6a0ebfe36bb1ad05e1df0e20b110de59c278498/urllib3-1.26.9-py2.py3-none-any.whl
Collecting idna<4,>=2.5; python_version >= "3" (from requests)
Downloading https://files.pythonhosted.org/packages/04/a2/d918dcd22354d8958fe113e1a3630137e0fc8b44859ade3063982eacd2a4/idna-3.3-py3-none-any.whl (61kB)
100% |████████████████████████████████| 61kB 5.9MB/s
Collecting charset-normalizer~=2.0.0; python_version >= "3" (from requests)
Downloading https://files.pythonhosted.org/packages/06/b3/24afc8868eba069a7f03650ac750a778862dc34941a4bebeb58706715726/charset_normalizer-2.0.12-py3-none-any.whl
Collecting certifi>=2017.4.17 (from requests)
Downloading https://files.pythonhosted.org/packages/11/dd/e015f3780f42dd9af62cf0107b44ea1298926627ecd70c17b0e484e95bcd/certifi-2022.5.18.1-py3-none-any.whl (155kB)
100% |████████████████████████████████| 163kB 5.9MB/s
Installing collected packages: urllib3, idna, charset-normalizer, certifi, requests
Successfully installed certifi-2022.5.18.1 charset-normalizer-2.0.12 idna-3.3 requests-2.27.1 urllib3-1.26.9
Step 9: Edit file /etc/letsencrypt/acme-dns-auth.py
Change first line:
#!/usr/bin/env python
to
#!/usr/bin/env python3
Step 10:
certbot certonly --manual --manual-auth-hook /etc/letsencrypt/acme-dns-auth.py \
--preferred-challenges dns --debug-challenges \
-d tutorialspots.com -d \*.tutorialspots.com
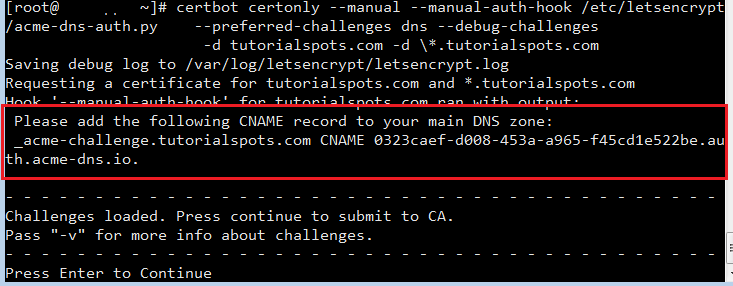
[root@tutorialspots ~]# certbot certonly --manual --manual-auth-hook /etc/letsencrypt/acme-dns-auth.py --preferred-challenges dns --debug-challenges -d tutorialspots.com -d \*.tutorialspots.com Saving debug log to /var/log/letsencrypt/letsencrypt.log Requesting a certificate for tutorialspots.com and *.tutorialspots.com Hook '--manual-auth-hook' for tutorialspots.com ran with output: Please add the following CNAME record to your main DNS zone: _acme-challenge.tutorialspots.com CNAME 0323caef-d008-453a-a965-f45cd1e522be.auth.acme-dns.io. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Challenges loaded. Press continue to submit to CA. Pass "-v" for more info about challenges. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Press Enter to Continue
Manual create CNAME record then check DNS here
When DNS available all check servers, Press Enter:
Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/tutorialspots.com/fullchain.pem Key is saved at: /etc/letsencrypt/live/tutorialspots.com/privkey.pem This certificate expires on 2022-09-01. These files will be updated when the certificate renews. Certbot has set up a scheduled task to automatically renew this certificate in the background. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - If you like Certbot, please consider supporting our work by: * Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate * Donating to EFF: https://eff.org/donate-le - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Method 2: (Step 6b-7b)
Step 6b:
certbot certonly --manual --preferred-challenges=dns --agree-tos -d tutorialspots.com -d \*.tutorialspots.com
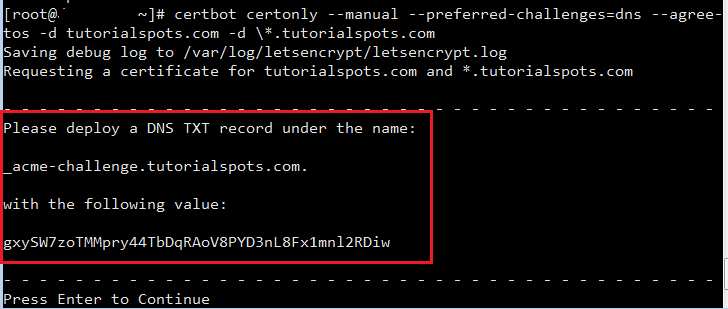
[root@downappz ~]# certbot certonly --manual --preferred-challenges=dns --agree-tos -d tutorialspots.com -d \*.tutorialspots.com Saving debug log to /var/log/letsencrypt/letsencrypt.log Requesting a certificate for tutorialspots.com and *.tutorialspots.com - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please deploy a DNS TXT record under the name: _acme-challenge.tutorialspots.com. with the following value: gxySW7zoTMMpry44TbDqRAoV8PYD3nL8Fx1mnl2RDiw - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Press Enter to Continue
Manual create TXT record then press enter
Step 7b:
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please deploy a DNS TXT record under the name: _acme-challenge.tutorialspots.com. with the following value: 7d_-au4ToHr0NCksznSqq8nN4UoGGwW_BAGQlYkpy-s (This must be set up in addition to the previous challenges; do not remove, replace, or undo the previous challenge tasks yet. Note that you might be asked to create multiple distinct TXT records with the same name. This is permitted by DNS standards.) Before continuing, verify the TXT record has been deployed. Depending on the DNS provider, this may take some time, from a few seconds to multiple minutes. You can check if it has finished deploying with aid of online tools, such as the Google Admin Toolbox: https://toolbox.googleapps.com/apps/dig/#TXT/_acme-challenge.tutorialspots.com. Look for one or more bolded line(s) below the line ';ANSWER'. It should show the value(s) you've just added. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Press Enter to Continue
Manual create second TXT record then check DNS here
When DNS available all check servers, press enter
Done!
Recommended to use method 1, to easily renew the certificate, you use step 10 to renew certificate




1 Comment
CentOS 7: use certbot to register SSL certificate for multiple domains with Cloudflare | Free Online Tutorials
(June 23, 2022 - 1:05 pm)[…] Step 1-5: CentOS 7: install certbot to register wildcard SSL certificate […]