Step 1:
cd /root yum install socat curl -y curl https://get.acme.sh | sh
Step 2:
acme.sh --issue -d tutorialspots.com -d *.tutorialspots.com --dns --force
If you get error:
It seems that you are using dns manual mode. Read this link first: https://github.com/acmesh-official/acme.sh/wiki/dns-manual-mode
Run
acme.sh --issue -d tutorialspots.com -d *.tutorialspots.com --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please
Result:
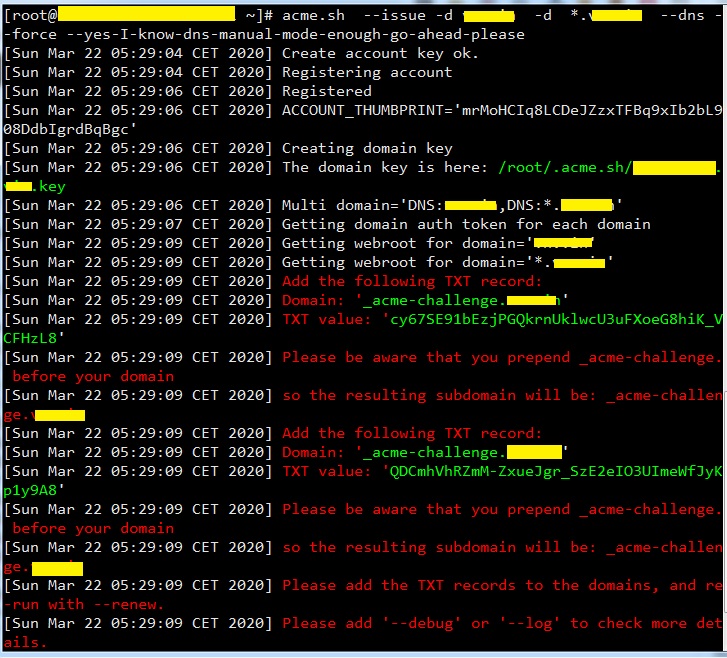
[root@tutorialspots ~]# acme.sh --issue -d tutorialspots.com -d *.tutorialspots.com --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please [Sun Mar 22 05:29:04 CET 2020] Create account key ok. [Sun Mar 22 05:29:04 CET 2020] Registering account [Sun Mar 22 05:29:06 CET 2020] Registered [Sun Mar 22 05:29:06 CET 2020] ACCOUNT_THUMBPRINT='mrMoHCIq8LCDeJZzxTFBq9xIb2bL908DdbIgrdBqBgc' [Sun Mar 22 05:29:06 CET 2020] Creating domain key [Sun Mar 22 05:29:06 CET 2020] The domain key is here: /root/.acme.sh/tutorialspots.com/tutorialspots.com.key [Sun Mar 22 05:29:06 CET 2020] Multi domain='DNS:tutorialspots.com,DNS:*.tutorialspots.com' [Sun Mar 22 05:29:07 CET 2020] Getting domain auth token for each domain [Sun Mar 22 05:29:09 CET 2020] Getting webroot for domain='tutorialspots.com' [Sun Mar 22 05:29:09 CET 2020] Getting webroot for domain='*.tutorialspots.com' [Sun Mar 22 05:29:09 CET 2020] Add the following TXT record: [Sun Mar 22 05:29:09 CET 2020] Domain: '_acme-challenge.tutorialspots.com' [Sun Mar 22 05:29:09 CET 2020] TXT value: 'cy67SE91bEzjPGQkrnUklwcU3uFXoeG8hiK_VCFHzL8' [Sun Mar 22 05:29:09 CET 2020] Please be aware that you prepend _acme-challenge. before your domain [Sun Mar 22 05:29:09 CET 2020] so the resulting subdomain will be: _acme-challenge.tutorialspots.com [Sun Mar 22 05:29:09 CET 2020] Add the following TXT record: [Sun Mar 22 05:29:09 CET 2020] Domain: '_acme-challenge.tutorialspots.com' [Sun Mar 22 05:29:09 CET 2020] TXT value: 'QDCmhVhRZmM-ZxueJgr_SzE2eIO3UImeWfJyKp1y9A8' [Sun Mar 22 05:29:09 CET 2020] Please be aware that you prepend _acme-challenge. before your domain [Sun Mar 22 05:29:09 CET 2020] so the resulting subdomain will be: _acme-challenge.tutorialspots.com [Sun Mar 22 05:29:09 CET 2020] Please add the TXT records to the domains, and re-run with --renew. [Sun Mar 22 05:29:09 CET 2020] Please add '--debug' or '--log' to check more details. [Sun Mar 22 05:29:09 CET 2020] See: https://github.com/acmesh-official/acme.sh/wiki/How-to-debug-acme.sh
Step 3:
Suppose that your server IP is 11.11.11.11
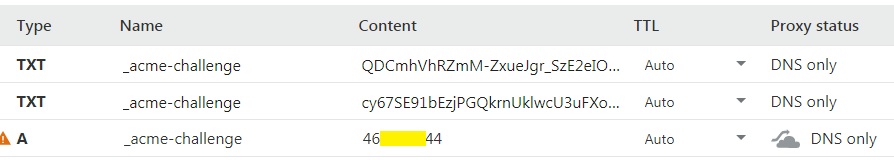
You must add 3 records for subdomain _acme-challenge.tutorialspots.com:
A record _acme-challenge.tutorialspots.com pointing to the server IP (11.11.11.11)
TXT record _acme-challenge.tutorialspots.com
value : “cy67SE91bEzjPGQkrnUklwcU3uFXoeG8hiK_VCFHzL8”
TXT record _acme-challenge.tutorialspots.com
value : “QDCmhVhRZmM-ZxueJgr_SzE2eIO3UImeWfJyKp1y9A8”
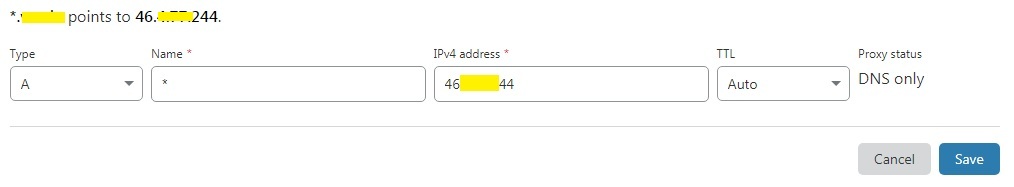
Step 4: Add wildcard dns
Step 5:
acme.sh --renew -d tutorialspots.com -d *.tutorialspots.com --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please
Result:
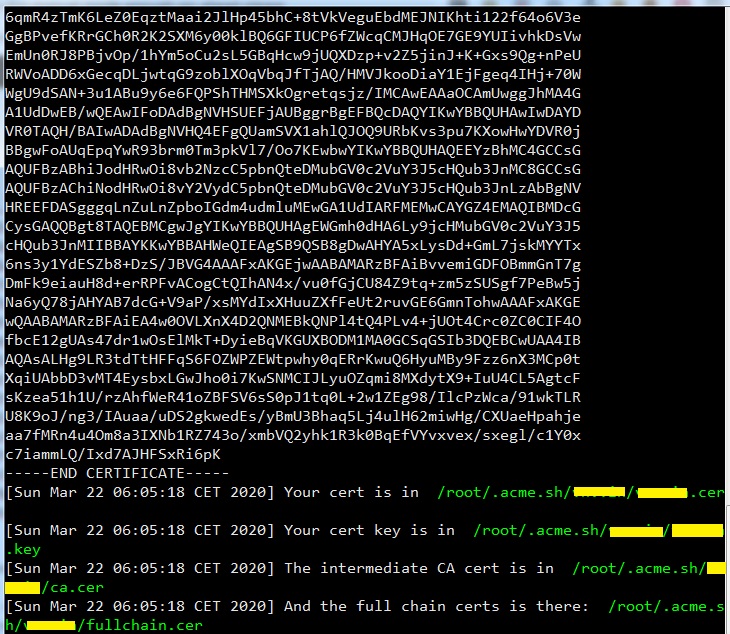
[root@tutorialspots ~]# acme.sh --renew -d tutorialspots.com -d *.tutorialspots.com --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please [Sun Mar 22 06:05:03 CET 2020] Renew: 'tutorialspots.com' [Sun Mar 22 06:05:04 CET 2020] Multi domain='DNS:tutorialspots.com,DNS:*.tutorialspots.com' [Sun Mar 22 06:05:04 CET 2020] Getting domain auth token for each domain [Sun Mar 22 06:05:04 CET 2020] Verifying: tutorialspots.com [Sun Mar 22 06:05:12 CET 2020] Success [Sun Mar 22 06:05:12 CET 2020] Verifying: *.tutorialspots.com [Sun Mar 22 06:05:16 CET 2020] Success [Sun Mar 22 06:05:16 CET 2020] Verify finished, start to sign. [Sun Mar 22 06:05:16 CET 2020] Lets finalize the order, Le_OrderFinalize: https://acme-v02.api.letsencrypt.org/acme/finalize/81234353/2737086269 [Sun Mar 22 06:05:17 CET 2020] Download cert, Le_LinkCert: https://acme-v02.api.letsencrypt.org/acme/cert/03e2c03c78d2db1504b7929e7a1d4aa68d02 [Sun Mar 22 06:05:18 CET 2020] Cert success. -----BEGIN CERTIFICATE----- MIIFTjCCBDagAwIBAgISA+LAPHjS2xUEt5Keeh1Kpo0BMA0GCSqGSIb3DQEBCwUA MEoxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MSMwIQYDVQQD ExpMZXQncyBFbmNyeXB0IEF1dGhvcml0eSBYMzAeFw0yMDAzMjIwNDA1MTdaFw0y MDA2MjAwNDA1MTdaMBExDzANBgNVBAMTBnZuLnZpbjCCASIwDQYJKoZIhvcNAQEB BQADggEPADCCAQoCggEBAMju9sBe7LQMyfhC1ZN5pv+e7CJRftuOcfaSpu6KVtGl 6qmR4zTmK6LeZ0EqztMaai2JlHp45bhC+8tVkVeguEbdMEJNIKhti122f64o6V3e GgBPvefKRrGCh0R2K2SXM6y00klBQ6GFIUCP6fZWcqCMJHqOE7GE9YUIivhkDsVw EmUn0RJ8PBjvOp/1hYm5oCu2sL5GBqHcw9jUQXDzp+v2Z5jinJ+K+Gxs9Qg+nPeU RWVoADD6xGecqDLjwtqG9zoblXOqVbqJfTjAQ/HMVJkooDiaY1EjFgeq4IHj+70W WgU9dSAN+3u1ABu9y6e6FQPShTHMSXkOgretqsjz/IMCAwEAAaOCAmUwggJhMA4G A1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwDAYD VR0TAQH/BAIwADAdBgNVHQ4EFgQUamSVX1ahlQJOQ9URbKvs3pu7KXowHwYDVR0j BBgwFoAUqEpqYwR93brm0Tm3pkVl7/Oo7KEwbwYIKwYBBQUHAQEEYzBhMC4GCCsG AQUFBzABhiJodHRwOi8vb2NzcC5pbnQteDMubGV0c2VuY3J5cHQub3JnMC8GCCsG AQUFBzAChiNodHRwOi8vY2VydC5pbnQteDMubGV0c2VuY3J5cHQub3JnLzAbBgNV HREEFDASgggqLnZuLnZpboIGdm4udmluMEwGA1UdIARFMEMwCAYGZ4EMAQIBMDcG CysGAQQBgt8TAQEBMCgwJgYIKwYBBQUHAgEWGmh0dHA6Ly9jcHMubGV0c2VuY3J5 cHQub3JnMIIBBAYKKwYBBAHWeQIEAgSB9QSB8gDwAHYA5xLysDd+GmL7jskMYYTx 6ns3y1YdESZb8+DzS/JBVG4AAAFxAKGEjwAABAMARzBFAiBvvemiGDFOBmmGnT7g DmFk9eiauH8d+erRPFvACogCtQIhAN4x/vu0fGjCU84Z9tq+zm5zSUSgf7PeBw5j Na6yQ78jAHYAB7dcG+V9aP/xsMYdIxXHuuZXfFeUt2ruvGE6GmnTohwAAAFxAKGE wQAABAMARzBFAiEA4w0OVLXnX4D2QNMEBkQNPl4tQ4PLv4+jUOt4Crc0ZC0CIF4O fbcE12gUAs47dr1wOsElMkT+DyieBqVKGUXBODM1MA0GCSqGSIb3DQEBCwUAA4IB AQAsALHg9LR3tdTtHFFqS6FOZWPZEWtpwhy0qERrKwuQ6HyuMBy9Fzz6nX3MCp0t XqiUAbbD3vMT4EysbxLGwJho0i7KwSNMCIJLyuOZqmi8MXdytX9+IuU4CL5AgtcF sKzea51h1U/rzAhfWeR41oZBFSV6sS0pJ1tq0L+2w1ZEg98/IlcPzWca/91wkTLR U8K9oJ/ng3/IAuaa/uDS2gkwedEs/yBmU3Bhaq5Lj4ulH62miwHg/CXUaeHpahje aa7fMRn4u4Om8a3IXNb1RZ743o/xmbVQ2yhk1R3k0BqEfVYvxvex/sxegl/c1Y0x c7iammLQ/Ixd7AJHFSxRi6pL -----END CERTIFICATE----- [Sun Mar 22 06:05:18 CET 2020] Your cert is in /root/.acme.sh/tutorialspots.com/tutorialspots.com.cer [Sun Mar 22 06:05:18 CET 2020] Your cert key is in /root/.acme.sh/tutorialspots.com/tutorialspots.com.key [Sun Mar 22 06:05:18 CET 2020] The intermediate CA cert is in /root/.acme.sh/tutorialspots.com/ca.cer [Sun Mar 22 06:05:18 CET 2020] And the full chain certs is there: /root/.acme.sh/tutorialspots.com/fullchain.cer
Now, you have 3 files in folder /root/.acme.sh/tutorialspots.com:
tutorialspots.com.cer <<=== Cert file
tutorialspots.com.key <<=== Private Key
fullchain.cer <<=== CA Chain file/bundle file
Step 6:
Config your http server:
Apache :
SSLCertificateFile /root/.acme.sh/tutorialspots.com/tutorialspots.com.cer SSLCertificateKeyFile /root/.acme.sh/tutorialspots.com/tutorialspots.com.key SSLCertificateChainFile /root/.acme.sh/tutorialspots.com/fullchain.cer
NGINX :
ssl_certificate /root/.acme.sh/tutorialspots.com/fullchain.cer; ssl_certificate_key /root/.acme.sh/tutorialspots.com/tutorialspots.com.key;
Renew certificate:
You use step 5
Automatic Renew certificate:
For more info about DNS API and how to do it visit this official page : https://github.com/Neilpang/acme.sh/tree/master/dnsapi Auto renew Let’s Encrypt certs via cron job : add this monthly cron for the auto renew check :
0 0 1 * * "/root/.acme.sh"/acme.sh --cron --home "/root/.acme.sh" > /dev/null




1 Comment
Use Let’s Encrypt certificate in VestaCP | Free Online Tutorials
(June 12, 2020 - 8:05 am)[…] Ia. Or you can install Let’s Encrypt Wildcard SSL […]